How the Petya Cyberattack Spread to America
It's similar to WannaCry -- but worse.
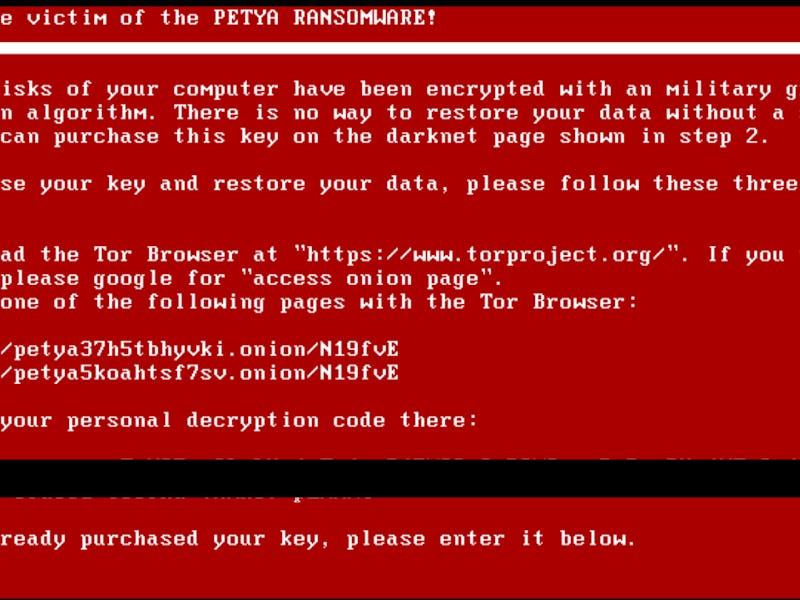
The massive Petya malware attack that spread from Russia and Ukraine to Western Europe on Tuesday has made it to the United States. How is this ransomware — which is a variation of the malicious Petya software, so many are now relabeling it “NotPetya” — spreading in the United States?
So far, American companies across at least five major industries have been affected: pharmaceuticals (Merck); advertising (WPP, which is based in Britain but has U.S. subsidiaries); legal (DLA Piper); medical (Pennsylvania’s Heritage Valley Health System); and shipping (APM Terminals, which is based in the Netherlands but operates ports in the United States). In all likelihood, that list will continue to grow.
While it’s not yet clear how the Petya malware first gets onto a network (though it doesn’t seem to be happening by email, unlike last month’s notorious WannaCry attack), security experts are pretty sure they know how it spreads once it’s there.
The virus affects the Windows operating system and “has a fake Microsoft digital signature appended to it,” reports Bloomberg. Petya takes advantage of EternalBlue, an “exploit” (software or commands that exploit a system vulnerability) that’s assumed to have been developed by the NSA and was leaked in April by the Shadow Brokers hackers. EternalBlue was also used in the WannaCry attack, and right now it’s spreading even in companies that recently installed a Microsoft patch to prevent another such assault.
Once the virus gets onto a computer, it works on “extracting passwords from memory or from the local filesystem,” reports Forbes, and uses those passwords to hack onto other computers on the same network. It also abuses PsExec, a tool that allows one computer to execute actions on remote devices, often through a system of “administrator” privileges.
The Russian security firm Kaspersky offered some explanations for how Petya operates and warned: “A single infected system on the network possessing administrative credentials is capable of spreading this infection to all the other computers through WMI or PSEXEC.”
The Petya attack seems to be designed to bribe victims into paying ransoms, although the Ukrainian government has a darker take and claims that the assault is meant to cause “the destabilization of the economic situation and […] the civic consciousness of Ukraine” and is merely “disguised as an extortion attempt.” The email address to which victims were supposed to send ransom payments has now been shut down by the provider, so people can’t pay up, even if doing so were a smart idea (the U.S. Computer Emergency Readiness Team insists that it is not).
Most popular antivirus tools fail to recognize Petya. “In a test of 61 antivirus solutions, only four successfully identified the ransomware,” reports The New York Times.
It already looks like this attack may do greater damage than WannaCry; it’s even affected the radiation monitoring at Chernobyl.
Although Petya isn’t yet contained, the United States may still escape debilitating damage, especially now that information about the malware is circulating and companies have a better idea of the warning signs for which they should look out.