The Sony Hackers Are Still Launching Attacks Around the World
The fluid cohort, dubbed the Lazarus Group, keeps morphing.
When a group of hackers dubbed the “Guardians of Peace” hacked Sony Entertainment in November, 2014, the entire world speculated that North Korea’s military was behind the back. The U.S. government even accused North Korea of bearing responsibility.
Now, a report out of cybersecurity firm Novetta sheds some light on the workings of the team behind the Sony attack, including why they seem to have suddenly vanished.
The report explains that the group may be operating under a variety of different aliases, including “NewRomanic Cyber Army Team” and “Who IsTeam.” But based on similarities between attacks that could only be the result of sharing information, it’s pretty clear that the same team that hacked Sony is still out there breaking into servers across the United States and Asia.
“There’s very hard evidence to suggest that a lot of the development is all originating from the same authors and codebases,” Andre Ludwig, a senior technical director at Novetta, told the Washington Post. “These aren’t pieces of malware that are being shared on underground forums — these are very well guarded codebases that haven’t leaked out or been thrown around publicly.”
Since the hackers assume a new identity for each project, the trackers at Novetta felt like the group was constantly rising from the dead. They’ve coined a new moniker for the team: the Lazarus Group.
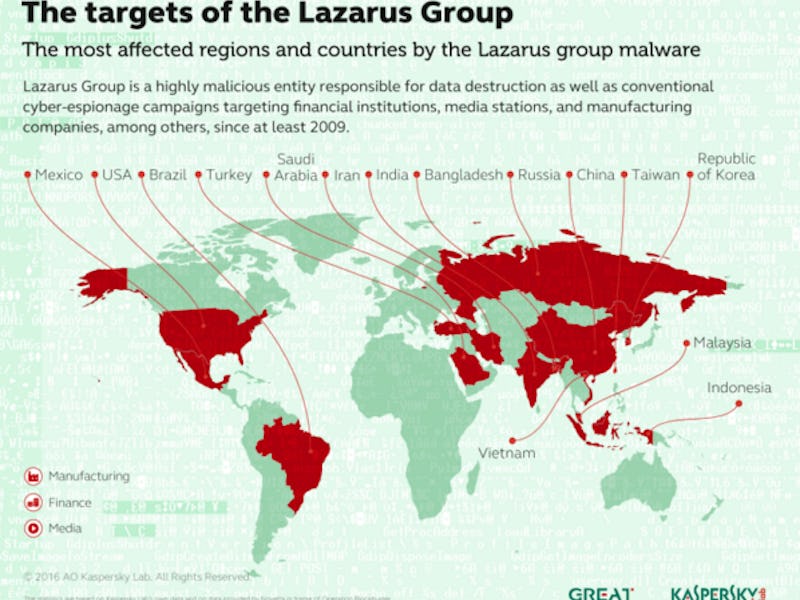
Novetta, along with AlienVault and Kaspersky Lab, has linked the Lazarus Group to a string of other attacks, including a 2013 attack on South Korean television studios and a “spearphishing” maneuver that used fake South Korean media. The focus on South Korea certainly supports the U.S. government’s assertion that the group is based around North Korea’s military. The Novetta report is oddly reticent about drawing such a conclusion, going only so far as to agree that it’s probably backed by some government.
“We believe the U.S. government assertion that [the Sony attack] was the work of a nation-state is far more likely than this being the work of a hacktivist group or a vindictive former employee,” said Novetta chief executive officer Peter LaMontagne told the Post.
It can be more difficult for security firms to draw hard conclusions about state actors, particularly because governments tend to have a wealth of additional, often classified, information that provides supporting evidence.
Sure, the group seems to work a typical Korean work day and exploited a bug in a uniquely Korean word processing system, but that’s not enough to say definitively that Kim Jong-un’s soldiers are typing away on the other side. The new report links Lazarus to attacks on China, perhaps North Korea’s only remaining ally, which would certainly amount to a strange provocation for the beleaguered communist state.
Nonetheless, Novetta still believes something must be done to prepare information systems to combat attacks from the Lazarus Group. The firm is launching “Operation Blockbuster” in partnership with other cybersecurity groups to help spread awareness of the group’s typical tactics.